
As organizations grow increasingly dependent on technology, the twin pillars of compliance and security have taken center stage. While often used interchangeably, these two concepts serve distinct purposes and are crucial to safeguarding trust.
As we step further into 2025, regulatory expectations and cyber threats are growing more sophisticated. This blog will unpack the key differences between compliance and security, explain why relying on one without the other is inadequate, and outline how combining both is critical for a robust cybersecurity posture.
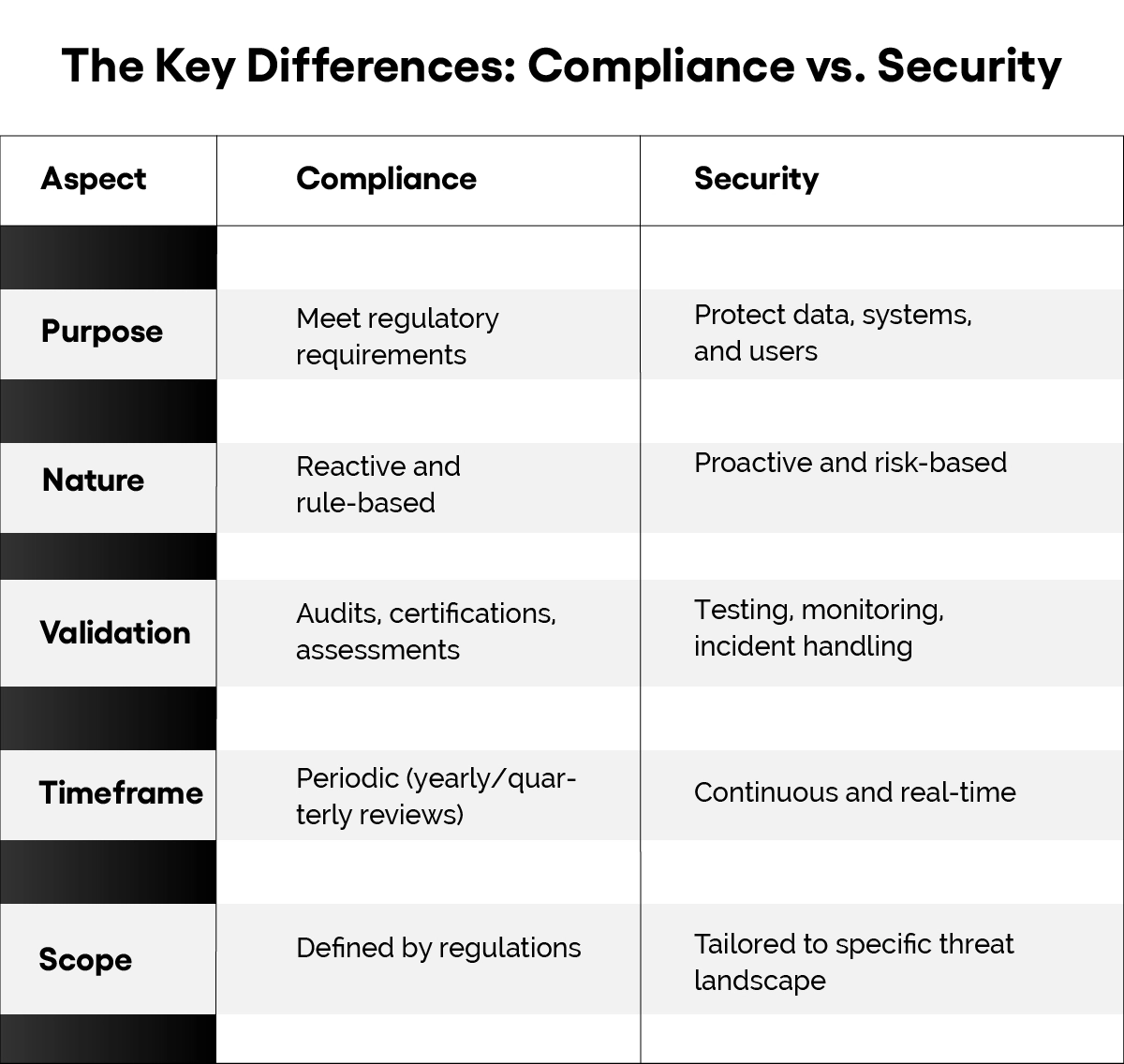
Understanding the Core Concepts
In building a resilient cybersecurity posture for an organisation in 2025, it is crucial to note the relationship of compliance and security within the broader context of a cyber defence framework. Let us define both terms.
What Is Compliance?
Compliance is the state of rest of an organisation with extrinsic legal, regulatory, and industrial criteria. Such rules are created to make sure that an organisation acts responsibly while managing sensitive information as well as stakeholder privacy and security.
Compliance is generally administered through:
- Regulations: Such as GDPR, HIPAA, or India’s Digital Personal Data Protection Act.
- Industry Standards: PCI DSS for payment card security or ISO/IEC 27001 on Information Security Management Systems.
- Audits and Assessments: Independent evaluation of an organisation against predetermined criteria.
Unlike a security strategy which provides a framework for reasonably protecting an organisation’s assets, compliance offers no such latitude. It is an absolute necessity as non-compliance can adversely affect an organisation legally and reputationally.
Yet, compliance is almost always point-in-time—having demonstrated that security controls existed during an audit, there is no assurance that current or future threats can be effectively countered.

What is security?
Security, in contrast, is the continuous process of protecting an organization’s digital assets—systems, data, infrastructure, and users—from internal and external threats. It is more about strategy and execution than regulatory checkboxes.
Security encompasses:
- Preventive Actions: Firewalls, encryption, access controls, and secure code development.
- Detective Actions: Security monitoring, Intrusion Detection Systems (IDS), and SIEMs.
- Responsive Measures: Incident response, breach containment, disaster recovery plans.
Security differs from externally driven compliance requirements because it adapts to an organisation’s unique threats and business model. It is always preemptive, never static, and requires constant attention every single day.
In summary, compliance drives you from a checklist perspective while security measures actual protection.
Why Compliance Alone Is Not Enough in 2025?
As of 2025, cyberattacks are no longer reserved for large corporations. Even small and medium-sized businesses, startups, and independent professionals are susceptible to advanced persistent threats, AI-driven phishing, and ransomware. Compliance checklists as an approach are no longer manageable.
While avoiding penalties may be achieved by compliance, they do not provide resilience against real-world cyberattacks. Numerous high-profile breaches have taken place within organisations that were, on paper, compliant. Why? Because loophole weaknesses or insider threats conflict with the ever-changing tactics used by threat actors regardless of compliance.
Security Without Compliance – A Risky Oversight
Fulfilling compliance requirements while providing advanced security through firewalls and intrusion detection systems is equally essential, as lack of either subjects organisations to significant risks.
Here’s why security alone isn’t enough:
- Regulatory Trouble
Robust non-compliance with regulations such as GDPR, HIPAA, and India’s DPDP Act will invoke hefty fines, legal action, or licence suspensions. - Missed Opportunities
In regulated industries, compliance is mandatory as a prerequisite for partnerships and market entry. Failing to prove compliance doesn’t only impact startups and SMEs but enables competition. - Reputation Risk
Non-compliance following a data breach can lead to an erosion of customer trust alongside credibility, granting security and compliance the ability to work in unison. - Audit Failures
Even the most secure firms, while lacking the necessary documentation and processes, subject themselves to external audits which can disrupt business operations and enforcement actions.
In 2025, a secure system still needs to be a compliant one. The two go hand-in-hand to truly safeguard your business.
How does compliance influence security?
While security aims to protect computer systems and data, compliance provides the comprehensive legal framework to direct and organise those efforts. Compliance in many ways serves as an architectural foundation blueprint to dominate effective security practices.
Similarities between them and where do they align?
While compliance and security serve different purposes, both need to work toward the same objective—safeguarding the data and mitigating risks. They also share several functions, which overlap and supplement one another.
Key Similarities:
Where They Align:
The 2025 Cyber Landscape: Converging Compliance and Security
As we advance into 2025, the boundary between compliance and security is increasingly interrelated. AI innovation, third parties, and previously low-risk industries are being targeted by threat actors. In response, authorities are implementing more security-heavy regulations.
What’s Driving the Convergence?
Building a Unified Strategy
In today’s environment of high uncertainty, organisations need to integrate compliance and security as two halves of a circle instead of two separate silos.
- Align Compliance With Its Respective Security Control – Use NIST, ISO 27001, or SOC 2 frameworks to cover and define the gaps you have between compliance, security, and other concurrent requirements.
- Perform Integrated Risk Evaluation – Combining the assessment of technical gaps and non-fulfilment of legal requirements results in silos, leaving unchecked gaps and exposing vulnerabilities.
- Automate Whenever Viable – Use available frameworks to monitor compliance in real time, manage vulnerabilities, and maintain checklists for audits.
- Participation of All Parties – It’s more than just legal compliance and IT security. Ensure that managerial people from HR and operations are brought to the strategic table and not just informed after decisions are made.
- Join Available Expertise – Engage with security vendors such as StrongBox IT and have them perform VAPT services to adhere to international standards and maintain compliance.
Conclusion
In the dynamic cyber landscape of 2025, compliance and security are two sides of the same coin. One ensures you’re operating within the law; the other ensures your business is resilient against real-world threats. Neglecting either exposes your organization to serious risk.
A unified approach doesn’t just help avoid penalties or prevent breaches — it builds customer trust, operational excellence, and long-term sustainability.
At StrongBox IT, we help organizations integrate compliance and security into a seamless strategy. Whether you’re looking to meet global standards or secure your digital infrastructure, our experts are here to guide you every step of the way.






