
In an era where cyber threats are becoming more frequent and complex, securing your business’s digital assets has never been more critical. Whether you’re a startup or an established enterprise, safeguarding sensitive data, customer trust, and regulatory compliance should be a top priority. One of the most effective ways to evaluate and strengthen your security posture is through Vulnerability Assessment Penetration Testing (VAPT).
This blog explores the essentials of VAPT testing – What is it, the different types, methodologies, and most importantly, why it’s indispensable for businesses in 2025 and beyond.
What is VAPT testing?
VAPT stands for Vulnerability Assessment and Penetration Testing. It is a two-step security testing process designed to identify, analyze, and mitigate vulnerabilities in an organization’s IT infrastructure, applications, and networks.
- Vulnerability Assessment (VA) focuses on identifying potential vulnerabilities in a system.
- Penetration Testing (PT) goes a step further by simulating real-world cyberattacks to exploit those vulnerabilities and understand the actual risk level.
Together, VAPT offers a comprehensive view of your security posture — identifying weaknesses before malicious hackers can exploit them.
Types of VAPT testing
VAPT can be performed on different aspects of an organization’s infrastructure. Here are the primary types:
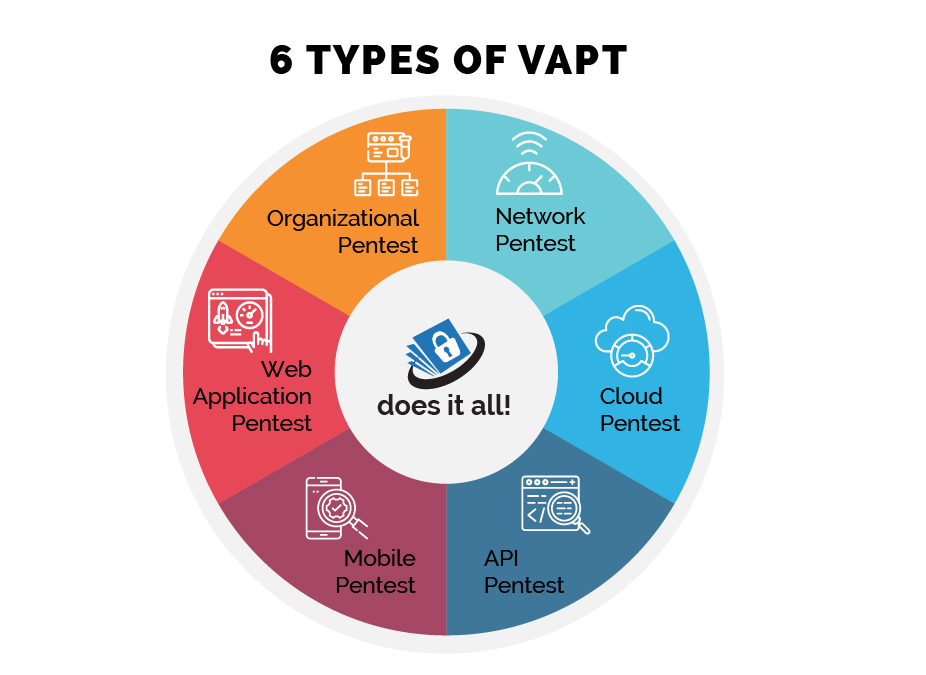
Importance of VAPT testing in 2025
Cybersecurity in 2025 isn’t just about antivirus software or firewalls. As digital transformation accelerates, cyberattacks have become more sophisticated — and frequent. Here’s why VAPT is more important than ever:
Proactive Risk Mitigation
VAPT helps businesses find vulnerabilities before attackers do, allowing them to act preemptively.
Regulatory Compliance
Standards like ISO 27001, GDPR, PCI-DSS, and India’s DPDP Act mandate regular security assessments.
Brand Trust and Reputation
A single breach can ruin customer trust. VAPT minimizes the risk of public data exposure.
Cost Savings
Preventing a cyberattack through early detection is far less costly than dealing with the aftermath of a breach.
Zero Trust & DevSecOps Adoption
VAPT aligns with modern security practices, helping businesses implement Zero Trust models and integrate security into the SDLC.
Understanding the difference between VA and PT
| Features | Vulnerability Assessment (VA) | Penetration Testing (PT) |
|---|---|---|
| Objective | Identify known vulnerabilities | Exploit vulnerabilities to assess risk |
| Approach | Automated scanning and reporting | Manual simulation of real-world attacks |
| Depth | Broader but shallow | Deep but narrow |
| Risk analysis | Limited context | Provides context based risk |
| Frequency | Regular scans | Typically annually or bi-annually |
Methodologies involved in VAPT testing
VAPT follows globally recognized standards and methodologies to ensure comprehensive coverage. The most common frameworks include:
- OWASP Top 10: Especially relevant for web and mobile application testing.
- PTES (Penetration Testing Execution Standard): A structured process covering pre-engagement to post-exploitation.
- NIST SP 800-115: Technical guide to security testing and assessment.
- OSSTMM (Open Source Security Testing Methodology Manual): A peer-reviewed security testing methodology.
Black Box Testing
Black Box Testing simulates an external attack by a hacker with no prior knowledge of the internal systems.
Characteristics:
- The tester knows nothing about the environment.
- Focuses on finding externally exploitable vulnerabilities.
- Time-consuming but reveals how an outsider could breach your defenses.
Use Case: Best for testing public-facing web apps, APIs, and external networks.
White Box Testing
White Box Testing involves complete access to the application’s source code, architecture, and internal documentation.
Characteristics:
- The tester has full knowledge of the system.
- Can analyze code for logical flaws, backdoors, and configuration issues.
- More comprehensive but less realistic in terms of attack simulation.
Use Case: Ideal for secure code reviews and when evaluating in-house applications.
Grey Box Testing
Grey Box Testing is a hybrid approach where the tester has partial knowledge of the system.
Characteristics:
- The tester has limited information (like user credentials or API documentation).
- Balances depth and realism.
- Helps simulate insider threats or privilege escalation attempts.
Use Case: Great for internal network assessments, authenticated web/mobile app testing.
Our VAPT testing process
At StrongBox IT, we follow a structured, hands-on VAPT methodology tailored to uncover both technical and business logic flaws. Our process ensures thorough vulnerability identification, real-world exploitation, and effective remediation. Here’s how we do it:
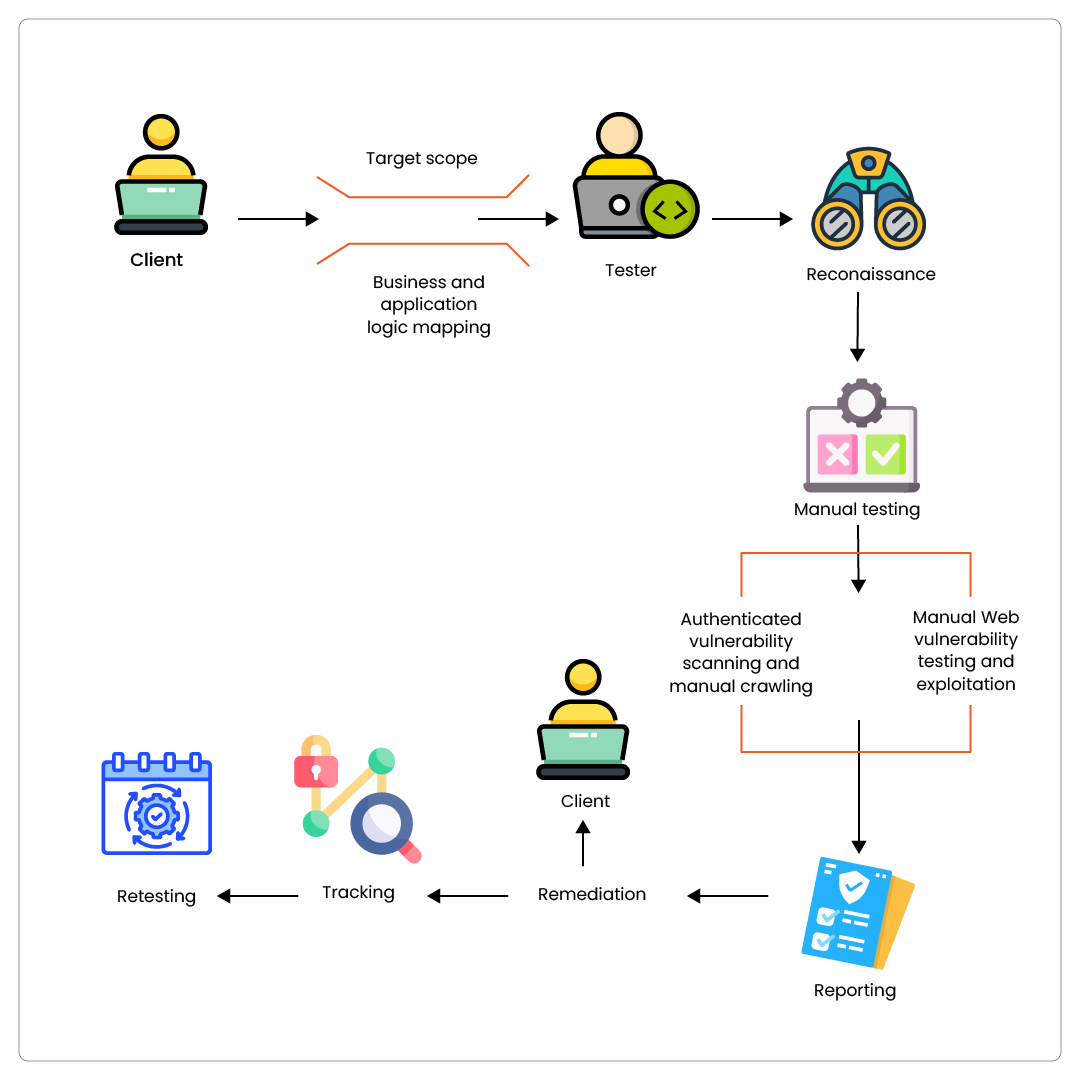
We begin by clearly defining the assets, environments, and applications to be tested. This includes:
- Web and mobile applications
- Internal and external networks
- APIs and cloud infrastructure
This step aligns business expectations with the technical scope to avoid coverage gaps.
We take time to understand how your application functions, including critical workflows like payments, user roles, or data handling. This helps uncover vulnerabilities that automated scanners typically miss, such as:
- Insecure direct object references (IDOR)
- Business logic bypass
- Broken access control
We perform passive and active reconnaissance to gather intel about your infrastructure. This includes:
- Subdomain enumeration
- Technology fingerprinting
- Open ports and exposed services
- Third-party integrations
This data helps us craft targeted attack vectors in later stages.
Our security analysts go beyond automation, performing manual inspection to identify nuanced vulnerabilities and edge cases, such as:
- Logic flaws
- Authorization bypasses
- Token manipulation
We prioritize manual techniques to simulate real-world attacker behavior.
We simulate real users with valid credentials to uncover flaws behind login walls. This includes:
- Session management issues
- Role-based access flaws
- Multi-factor authentication testing
Manual crawling ensures complete coverage of dynamic content and hidden inputs that automated tools may overlook.
Using the OWASP Top 10 and beyond, we manually test for:
- SQL Injection
- Cross-Site Scripting (XSS)
- Insecure Deserialization
- SSRF, RCE, IDOR
- Broken authentication
We responsibly exploit vulnerabilities to demonstrate actual impact, not just theoretical risk.
We provide a comprehensive, human-readable report that includes:
- Vulnerability descriptions
- Business impact analysis
- Technical risk rating (CVSS/CWE references)
- Proof-of-concept (PoC) screenshots/videos
- Step-by-step remediation guidelines
Our experts work with your development and IT teams to ensure effective patch implementation. We also provide security consulting to guide secure coding best practices.
We maintain a secure tracker to monitor remediation progress and ensure accountability. Clients get visibility into:
- Pending fixes
- In-progress items
- Verified resolutions
This step bridges the gap between detection and defense.
Once fixes are applied, we perform a comprehensive retest to:
- Confirm all vulnerabilities are resolved
- Ensure no new issues were introduced
- Certify the application/environment as secure
We issue a final attestation report, validating that your digital assets are protected.

Here are the 6 ways in which VAPT can be helpful for your business
Vulnerability Assessment and Penetration Testing (VAPT) is more than just a checkbox in your cybersecurity checklist—it’s a proactive shield that safeguards your business from ever-evolving threats. Here’s how VAPT can give your organization a serious edge:
Conclusion
Vulnerability Assessment and Penetration Testing (VAPT) isn’t just about finding weaknesses; it’s about fortifying your business, preserving customer trust, and staying ahead of regulatory demands. With threats evolving faster than ever, periodic and thorough VAPT is your best line of defense.
At StrongBox IT, we don’t just run tests—we uncover risks that others miss, simulate real-world attack scenarios, and work alongside your teams to close security gaps with precision. Whether you’re a growing startup or an established enterprise, our tailored VAPT services are designed to protect what matters most to your business.
Get in touch with StrongBox IT today to assess your current security posture and take the first step toward a safer, more resilient digital future.






